We make an attack on an Android phone. Android. Review of combat applications. Wireless network analysis


Application for protection against interception and redirection of traffic.
ARP Guard (WiFi Security). Many people know how easily passwords, logins and session IDs are intercepted when the attacker is on the same network as the target. Under certain circumstances, someone can even gain access to the device by simply replacing the update. Using a VPN channel and encryption solve the problem to some extent. However, various network pranks, such as “disabling Internet access,” will still work. ARP Guard will allow you to forget about the dangers that lurk in open networks, and enjoy comfortable Internet surfing. The program is easy to use and does not require any special knowledge. Moreover, in the basic protection mode you won’t even need superuser (root) rights.
The program has two protection modes. Working in the first mode, the application will warn of danger if an attack is detected. At the same time, the user does not have to be the owner of a rooted device. In the second mode, the program makes the protected device invulnerable to ARP Spoofing attacks. No warnings, Wi-Fi shutdowns, or other precautions will be required. An attacker simply will not be able to direct traffic through himself. In this case, the device will become immune, including to dirty tricks like wi-fi kill and other “Internet shutdowns”.
The launch button is a large red shield that will turn green once the protection is activated. Below is a monitoring panel that displays the connection status, as well as the IP and MAC addresses of the device and gateway. It's time to launch the program, once and for all protecting your device from pests.
Unfortunately, the user receives the opportunity to add a monitoring icon to the status bar, as well as a guarantee of constant operation of the service, only after purchase. However, even out of the box, all the main functionality of the program is available.
In the settings you can configure attack notifications, as well as set automatic shutdown Wi-Fi when using non-root operating mode. After the purchase, three additional functions will become available - displaying an icon with monitoring, autostarting the program when the device is rebooted, and guaranteeing the constant operation of the service. Once you launch a program, you can forget about its existence forever.
At the very bottom are the “expert” settings. On this moment This is the ability to enable/disable BSSID analysis. This function is needed to prevent an attack launched before the protected device is connected to the network. This is possible in small networks with a limited number of constantly connected nodes, if someone has previously learned the IP address of the device during previous connections. However, in large or "public" networks you don't have to worry about this. Using BSSID analysis requires caution. You must first make sure that the access point serves as a gateway. For continuous operation, especially in root mode, it is strongly recommended to leave this function inactive.
That's how it works. If it were not for ARP Guard, right now someone could write messages in topics on behalf of the device owner simply by intercepting a request to a site containing a cookie. Of course this is a joke. The screenshot was taken during a test, and yet another time the “attacker” could be anyone. I would like to note that in root operating mode no warnings will be displayed. Such attacks will simply become impossible, since the gateway will be registered statically every time you connect to the network.
Now, in order to protect yourself on “public” networks, there is no need to set up a VPN or use ready-made clients that pass traffic through the developer’s server. Moreover, you won't have to do anything at all. ARP Guard will take care of security and will not allow network pests to pester users with unpleasant pranks. ARP Guard - free program, which runs completely in the background. The application contains paid content, which boils down to functions that ensure constant operation of the service, as well as disabling advertising.
Peculiarities.
5 minutes to read.
Hello everyone, dear readers. Today we will touch on a very specific and hot topic, namely hacker programs for mobile gadgets on the Android operating system. These Android programs allow you to perform some hacking actions.
Attention: a selection of these programs is presented here for informational purposes only. You use all applications from the collection at your own peril and risk. Also, links to hacker programs are not published for the safety of your Android mobile devices.
The developer of this Android program is famous developer software by Andreas Koch. This application designed to intercept and hack a browser session. To make it work, just install it from the application store, open it and click the Start button, after which it will begin scanning sessions that are suitable for hacking.
By the way, the application works with many popular sites: Amazon, Facebook, Flickr, Twitter, Linkedin, Yahoo, Live, Vkontakte, as well as Google branded sites, which are not encrypted by the developer himself! Why is Droidsheep needed? - you ask. Everything is quite simple, for example, you urgently need to send a message from another person’s phone, but you cannot do this, since it is blocked and its owner has moved away.
Being on the same Wi-Fi network, you can access his phone through the program and perform the operation you need in just a few clicks on the screen of your smartphone!
It was created to quickly (literally instantly) check the license of any Android Market and gain access to it, emulate (falsely make) purchases within it ( this opportunity available only for the online market from which the applications were officially downloaded or purchased).
If we talk in simple words, then if you're tired permanent offers about purchasing an additional contact, then you can remove them using Freedom, or vice versa, you want to make a purchase for free and again, Freedom is best suited for these purposes. For the application to work, you just need to install it (it is not in the application store) and get root rights to your device.
And Voila! You can now make purchases for free or remove all reminders about them altogether. Also, for such an adventure, of course, you need Google Apps c Google Play Store and Google Service Framework, and, accordingly, himself Google Account.
Anonymous Hackers Android is official Android an application from an anonymous but well-known group of hackers that gives you quick, and most importantly, secure access to latest news Anonymous Hackers Group, videos, events, messages and more.
Application features:
- Anonymous Youtube channel, but the court always has the latest informational videos available.
- News is updated daily and you are guaranteed to have access to the most reliable and latest events.
- Updates to your social networks(Facebook and Twitter).
- And much more.
What should you do if you urgently need to access the global web, and the only way to connect to the Internet is a secure router for wireless transmission data. Well, get around this blocking The quite useful Wireless cracker application for Android will help you.
The program is available for download in the Google Play app store and is absolutely free! Launching the program is quite simple: you need to log in by first registering on the official website of the application. As a result, the user gets the opportunity to access any wireless access point, but this all sounds easy and simple in theory.
In practice, it turns out that gaining access to a protected point is not so easy, since the application can only calculate the standard password (for example, TPLINKart - 30000) that was installed on it by the manufacturer.
That is, the application will not be able to guess the password that the owners of the router themselves set.
Anti - Android Network Toolkit. By her own this program consists of only 2 parts: the program itself and accessible, extensible plugins. It is important to know: the upcoming major update will add functionality, new plugins or vulnerabilities/exploits.
As you probably already understood, even a novice user who has difficulty navigating the software, since almost every time (no one canceled the failures during the program’s operation) you start it, Anti displays a completely complete map of your entire network, searches for active devices and vulnerabilities, and displays the relevant information.
It is important to know: many people do not know about the significance of flowers. For example, a green LED indicates overly active devices, yellow indicates available ports, and red indicates vulnerabilities found.
In addition, each device will have an icon indicating the type of device, after the scan is completed, Anti will generate an automatic report indicating the vulnerabilities you have or bad practices in use, and tell you how to fix each of them.
There is no protection from the Internet while the device is connected to the network. Ensuring security in our time is one of the main tasks, so many third party applications to improve it.
The following apps will help protect your Android devices from security and privacy threats.
List of apps to protect Android devices
1. Avast Mobile Security
Avast is an excellent application for protecting your phone on Android based from viruses and other threats.
Avast is one of the most popular free antiviruses for Android. It notifies you about the installation of spyware and adware that threaten the security of your personal data.
The probability of detecting the latest malware is approximately 99.9%, and in the case of malware that appeared within a month, the probability is almost 100%.
Conclusion: If you need protection against malware and for safe browsing, then this application is suitable for you.
2. Sophos Antivirus and security
Sophos is one of the best free antiviruses for Android.
The user interface may be underwhelming. However, the functionality will allow you to stop worrying about security.
Possibilities:
- scanning for viruses of installed and existing applications, as well as data storages;
- protection against loss and theft with support remote access, allowing you to format, block, enable sound signal on your device or set its location;
- web content filtering;
- spam blocking.
Conclusion: If useful features If a nice design is more important to you, then you won’t find much better than Sophos.
3.AppLock
This application is quite easy to use. AppLock protects individual apps from hackers by requiring a PIN or graphic key. In this way you can protect SMS, contacts, Gmail, and indeed any application.Do not confuse this application lock with the device lock built into the phone. Built-in lock locks the entire phone. No access to any applications. In turn, AppLock allows you to block your favorite applications.

Conclusion: If you require prevent intruders from accessing to individual applications, but you do not want to password protect the device as a whole, then Applock is suitable for this.
4. Signal Private Messenger
There are many secure messaging apps available. Most of them only work if both users are using the same application.However, Signal Private Messenger allows you to add additional level of protection to regular SMS, even if one of the users does not use Signal Private Messenger. The application is developed by Open Whisper System.

The application has the following features:
- open source;
- end-to-end encryption. Nothing is stored on the application server;
- encryption is possible even if one of the users does not have Signal Private Messenger.
5. Secure Call
Ensures that no one can listen to calls. Secure Call provides end-to-end encryption of calls to prevent eavesdropping by unauthorized persons.
The application is used by default for incoming and outgoing calls. Thanks to decentralized architecture(peer-to-peer) with reliable end-to-end encryption, no unauthorized persons will be able to listen to your calls, including the application developers themselves.
Conclusion: If you need end-to-end encrypted calls, use Secure Call.
6. App Ops
The main function of App Ops is to revoke a specific set of permissions from selected applications. Many apps ask for additional permissions that are in no way related to their functionality.App Ops allows you to block excessive powers. When installing an application, you must allow access to everything that the application requires.

If you deny any permission, the application will not be installed. App Ops will help you out if you need to install applications without giving certain permissions.
Conclusion: App Ops will address the issue of revoking specific unnecessary permissions.
7. Lastpass
Everyone today has multiple accounts and passwords. It's not easy to remember them all.LastPass is one of the best available on the market password managers. Additional levels of protection are applied when storing passwords.

All your confidential data is available to you from any computer or mobile device. Passwords are encrypted with one master password. To gain access to all passwords, you only need to remember your LastPass password.
Conclusion: A simple solution to store all your passwords.
8. Android Device Manager
Android Device Manager allows you to turn on the sound signal, determine the location, and lock your Android device. The app also allows you to delete all data from the device in case the phone is no longer under your control.In many applications this is implemented as additional function. Nevertheless, Google app easier to install. Also, it allows you to log into your account through someone else's device and delete all data on the go.
Android. Overview of combat applications
Alexander Antipov
Capture Software Overview Wi-Fi networks With Android devices from Alexander Navalikhin, Positive Research Center
Good day!
Along with the article "", an almost similar article about Android was born.
We already know what the iPhone is capable of. Is Android inferior to it?
About 25 combat applications were reviewed. I would like to provide you with the result of a small study. Many applications did not even launch, some froze the phone, but some even worked! All software was tested on an LG Optimus phone, with Android version 2.3.
So, short review combat software on Android:
1. Shark- The same one. Yes, it is also available for Android. Works flawlessly. The device started up without problems. Writes logs in *.pcap format. Adds to sdcard. The file can be easily parsed as windows car, and on the phone itself, using Sharck Read. ( Good application. Especially if the phone works in Wi-Fi quality access points.)

2. / - Interception of web sessions. Quite simple, but sensational applications. We cling to an open point, launch and wait... By the way, sometimes you can hang the point itself.
3. - An application from the must-have series. Scans the entire subnet you are on. Displays a list of devices. Select the one you don’t like, click on the checkbox and wait a couple of seconds. The device remains without the Internet.

4. - Changes your MAC. Works well in conjunction with step 3.
5. / - Scans wireless networks, displays a list of connected devices. It can scan each device separately and provide a list of open ports. The vessels include ping, trace, wake on lan, arp, udp-flood.

6. - Beautiful application. Displays all available access points, SSID, mac, encryption, signal strength.

7. - Allows you to edit /etc/hosts. Useful application, especially when the phone acts as a Wi-Fi point.

8. - web server. Works well together with point 7.
9. - Real BruteForce on Android! Each application tries to force Basic Access Authentication. The software itself is a little damp. But I got through my point, with the password 12345, quite easily and quickly. For normal operation- don't forget to download a good dictionary.
10. - selects pre-installed WPA/WEP access keys for your Android smartphone from nearby routers. Works well with standard Thomson, DLink, Pirelli Discus, Eircom, Verizon FiOS.
11. - Universal application. Network scanner, sniffer, MITM, Remote Exploits! Expandable functionality through plugins. The more functionality, the more money She is standing.
Most of the applications require root rights.
This article is written for informational purposes!
“A smartphone with hacking tools? There is no such thing,” we would have told you just recently. It was possible to launch the usual tools for implementing attacks only on some Maemo. Now many tools have been ported to iOS and Android, and some hack-tools have been specially written for the mobile environment. Can a smartphone replace a laptop in penetration tests? We decided to check it out.
Android is a popular platform not only for mere mortals, but also for the right people. Quantity useful utilities It's just overwhelming here. For this we can thank the UNIX roots of the system, which greatly simplified the porting of many tools to Android. Unfortunately, Google does not allow some of them into the Play Store, so you will have to install the corresponding APK manually. Also, some utilities require maximum access to the system (for example, the iptables firewall), so you should take care of root access in advance.
Each manufacturer uses its own technology here, but finding the necessary instructions is quite easy. A good set of HOWTOs was put together by the LifeHacker resource (bit.ly/eWgDlu). However, if you couldn’t find a particular model here, the XDA-Developers forum (www.xda-developers.com) always comes to the rescue, where you can find various information on virtually any model of Android phone. One way or another, some of the utilities described below will work without root access. So, we present to you hacking utilities for Android.
Package Manager:

Let's start the review with an unusual package manager. The developers call it “utilities for superusers,” and this is not far from the truth. After installing BotBrew, you get a repository from where you can download a huge number of familiar tools compiled for Android. Among them: Python and Ruby interpreters for running numerous tools that are written in them, a tcpdump sniffer and an Nmap scanner for network analysis, Git and Subversion for working with version control systems, and much more.
Network scanners:

An inconspicuous smartphone, which, unlike a laptop, fits easily into a pocket and never raises suspicion, can be useful for network exploration. We have already said above how you can install Nmap, but there is another option. PIPS is a port specifically adapted for Android, although it is an unofficial port Nmap scanner. This means you can quickly find active devices on the network, determine their OS using fingerprinting options, perform a port scan - in short, do everything that Nmap is capable of.
l
There are two problems with using Nmap, despite all its power. Firstly, the parameters for scanning are transmitted through launch keys, which you must not only know, but also be able to enter using an inconvenient mobile keyboard. And secondly, the scanning results in the console output are not as clear as we would like. The Fing scanner does not have these shortcomings; it very quickly scans the network, does fingerprinting, and then displays a list of all available devices, dividing them by type (router, desktop, iPhone, and so on). At the same time, for each host you can quickly view a list of open ports. Moreover, right from here you can connect, say, to FTP, using the FTP client installed in the system - very convenient.

When we're talking about When analyzing a specific host, the NetAudit utility can be indispensable. It works on any Android device (even non-rooted) and allows you not only to quickly identify devices on the network, but also to examine them using a large fingerprinting database to identify operating system, as well as CMS systems used on the web server. There are now more than 3,000 digital fingerprints in the database.


If, on the contrary, you need to work at a lower level and carefully examine the operation of the network, then you cannot do without Net Tools. It is indispensable at work system administrator a set of utilities that allows you to fully diagnose the operation of the network to which the device is connected. The package contains more than 15 different types of programs, such as ping, traceroute, arp, dns, netstat, route.
Wi-fi monitor mode in android:
All WiFi modules have a special monitor mode. This mode can also be used for sniffing, intercepting and cracking passwords. However, in Android devices, due to hardware limitations, access to this mode is closed. The fact is that in most Android smartphones the same ones from Broadcom are used - these are bcm4329 or bcm4330, which do not work in a completely standard way.
The website contains instructions for activating monitor mode on Nexus One (Cyanogen 7) and GS2 (Cyanogen 9). Ready-made packages can be downloaded.
To run the code on other devices, you need to download the source code yourself and compile the package.
TRAFFIC MANIPULATIONS:

The tcpdump-based sniffer honestly logs all data into a pcap file, which can then be studied using familiar utilities like Wireshark or Network Miner. Since no capabilities for MITM attacks are implemented in it, it is rather a tool for analyzing your traffic. For example, this is a great way to study what programs installed on your device from dubious repositories transmit.

If we talk about combat applications for Android, then one of the most sensational is FaceNiff, which implements interception and injection into intercepted web sessions. By downloading the APK package with the program, you can run this hack tool on almost any Android smartphone and, by connecting to a wireless network, intercept accounts of a variety of services: Facebook, Twitter, VKontakte, and so on - more than ten in total. Session hijacking is carried out using the ARP spoofing attack, but the attack is only possible on unprotected connections (FaceNiff is not able to wedge into SSL traffic). To curb the flow of scriptkidies, the author limited the maximum number of sessions to three.
l
If the creator of FaceNiff wants money for using it, then DroidSheep is completely free tool with the same functionality. True, you won’t find the distribution kit on the official website (this is due to Germany’s harsh laws regarding security utilities), but it can be found on the Internet without any problems. The main task of the utility is to intercept user web sessions of popular social networks, implemented using the same ARP Spoofing. But there’s a problem with secure connections: like FaceNiff, DroidSheep flatly refuses to work with the HTTPS protocol.

This utility also demonstrates the insecurity of open wireless networks, but on a slightly different plane. It does not intercept user sessions, but allows HTTP traffic to pass through itself using a spoofing attack, performing specified manipulations with it. Starting from ordinary pranks (replacing all the pictures on the site with trollfaces, flipping all the images or, say, replacing Google results) and ending with phishing attacks, when the user is given fake pages of such popular services as facebook.com, linkedin.com, vkontakte.ru and many others.

If you ask which hack utility for Android is the most powerful, then Anti probably has no competitors. This is a real hacker combine. The main task of the program is to scan the network perimeter. Next, various modules enter the battle, with the help of which a whole arsenal is implemented: eavesdropping on traffic, carrying out MITM attacks, and exploiting found vulnerabilities. True, there are also disadvantages. The first thing that catches your eye is that the exploitation of vulnerabilities is carried out only from the central program server, which is located on the Internet, as a result of which targets that do not have an external IP address can be forgotten.
TRAFFIC TUNNELING:
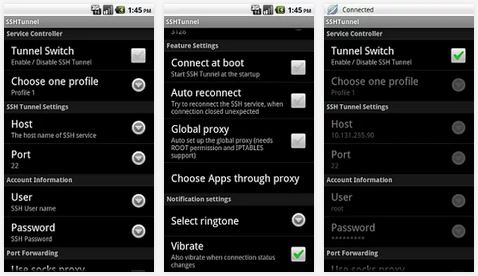
Okay, but how can you ensure the security of your data that is transmitted over an open wireless network? In addition to VPN, which Android supports out of the box, you can create an SSH tunnel. For this purpose, there is a wonderful SSH Tunnel utility, which allows you to route the traffic of selected applications or the entire system as a whole through a remote SSH server.

It is often necessary to send traffic through a proxy or SOX, and in this case ProxyDroid will help out. It's simple: you choose which application traffic you want to tunnel, and specify a proxy (HTTP/HTTPS/SOCKS4/SOCKS5 are supported). If authorization is required, ProxyDroid also supports this. By the way, the configuration can be bound to a specific wireless network by doing different settings for each of them.
WIRELESS NETWORK:

The built-in wireless network manager is not very informative. If you need to quickly get a complete picture of nearby access points, then Wifi utility Analyzer is a great choice. It will not only show all nearby access points, but will also display the channel on which they operate, their MAC address and, most importantly, the type of encryption used (having seen the coveted letters “WEP”, we can assume that access to the secure network is provided ). In addition, the utility is ideal if you need to find where the desired access point is physically located, thanks to a visual signal strength indicator.

This utility, as its developer claims, can be useful when the wireless network is filled to capacity with clients, and it is at this moment that a good connection is needed and stable connection. WiFiKill allows you to disconnect clients from the Internet either selectively or based on a specific criterion (for example, it is possible to make fun of all the Yabloko members). The program simply performs an ARP spoofing attack and redirects all clients to themselves. This algorithm is stupidly simply implemented on the basis of iptables. This is the control panel for fast food wireless networks.
WEB APPLICATION AUDIT:

Manipulating HTTP requests from a computer is a piece of cake; there are a huge number of utilities and browser plugins for this. In the case of a smartphone, everything is a little more complicated. HTTP Query Builder will help you send a custom HTTP request with the parameters you need, for example, the desired cookie or a changed User-Agent. The result of the request will be displayed in a standard browser.

If the site is password protected using Basic Access Authentication, then you can check its reliability using the Router Brute Force ADS 2 utility. Initially, the utility was created to brute force passwords on the router admin panel, but it is clear that it can be used against any other resource with similar protection . The utility works, but is clearly crude. For example, the developer does not provide for brute force, but only brute force using a dictionary.

Surely you have heard about such a program for disabling web servers as Slowloris. The principle of its operation is to create and maintain maximum amount connections to a remote web server, thus preventing new clients from connecting to it. So, AnDOSid is an analogue of Slowloris right in your Android device! It's sad, but two hundred connections is often enough to render one in four Apache websites unstable.
VARIOUS USES:

When working with many web applications and analyzing their logic, it is quite common to encounter data transmitted in encoded form, namely Base64. Encode will help you decode this data and see what exactly is stored in it. Perhaps, by substituting quotes, encoding them back into Base64 and substituting them in the URL of the site you are researching, you will get the coveted database query error.

If you need a hexadecimal editor, then there is one for Android too. With HexEditor you can edit any files, including system files, if you elevate the program's rights to superuser. An excellent replacement for a standard text editor, allowing you to easily find the desired piece of text and change it.
REMOTE ACCESS:

Once you have access to a remote host, you need to be able to use it. And for this we need clients. Let's start with SSH, where ConnectBot is already the de facto standard. In addition to a convenient interface, it provides the ability to organize secure tunnels via SSH connections.

A useful program that allows you to connect to a remote desktop via RDP or VNC services. I’m very glad that these are two clients in one; there is no need to use different tools for RDP and VNC.

Specially written for Android browser MIB, with which you can manage network devices using the SNMP protocol. It can be useful for developing an attack vector on various routers, because the standard community string (in other words, an access password) for management via SNMP has not yet been canceled.
IPHONE
The iOS platform is no less popular among security utility developers. But if in the case of Android rights While root was needed only for some applications, jailbreak is almost always required on Apple devices. Fortunately, even for latest firmware iDevices (5.1.1) already has a jailbreak tool. Together with full access You also get an alternative application manager, Cydia, which already contains many utilities.
OPERATING THE SYSTEM:

The first thing I want to start with is installing the terminal. For obvious reasons, it is not included in the standard delivery of the mobile OS, but we will need it to run console utilities, which we will discuss further. The best implementation of a terminal emulator is MobileTerminal - it supports multiple terminals at once, gestures for control (for example, for sending

Another, more complex option to gain access to the device's console is to install OpenSSH on it (this is done through Cydia) and connect to it locally through an SSH client. If you use the right client like iSSH, which has amazing touchscreen control, you can work with the local console and remote hosts from one place.
DATA INTERCEPTION:

Now that you have access to the console, you can try the utilities. Let's start with Pirni, the first full-fledged sniffer for iOS. The structurally limited Wi-Fi module built into iDevices cannot be switched to the promiscuous mode necessary for normal data interception. So for sniffing, classic ARP spoofing is used, with the help of which all traffic is passed through the device itself. The standard version of the utility is launched from the console, but there is a more advanced version - Pirni Pro, which boasts graphical interface. Moreover, it can parse HTTP traffic on the fly and even automatically pull out interesting data from there (for example, logins and passwords), using regular expressions, which are set in the settings.

The well-known sniffer Intercepter-NG has recently had a console version that works on iOS and Android. It already implements grabbing passwords transmitted over a variety of protocols, intercepting instant messenger messages, and also resurrecting files from traffic. At the same time, network scanning functions and high-quality ARP Poison are available. To work, you must first install the libpcap package via Cydia. All startup instructions boil down to setting the correct rights: chmod +x intercepter_ios. Next, if you run the sniffer without parameters, a clear interactive interface will appear.

It's hard to believe, but this one the most complex instrument To implement MITM attacks, everything was ported to iOS. After a tremendous amount of work, we managed to make a full-fledged mobile port. To save yourself from dancing with a tambourine around dependencies during self-compilation, it is better to install an already built package using Cydia, after adding heworm.altervista.org/cydia as a data source. The kit also includes the etterlog utility, which helps to extract various types of traffic from the collected dump. useful information(for example, FTP accounts).
WIRELESS NETWORK ANALYSIS:

In old iOS versions craftsmen ran aircrack and could break the WEP key, but we checked: the program does not work on new devices. Therefore, to study Wi-Fi, we will have to be content with only Wi-Fi scanners. WiFi Analyzer analyzes and displays information about all available 802.11 networks around you, including information about SSID, channels, vendors, MAC addresses and encryption types. With such a program it is easy to find the physical location of the point if you suddenly forget it, and, for example, look at the written WPS PIN required for connection.
NETWORK SCANNARS:

What program does any penetration tester use anywhere in the world, regardless of goals and objectives? Network scanner. And in the case of iOS, this will most likely be the most powerful Scany toolkit. Thanks to a set of built-in utilities, you can quickly get a detailed picture of network devices oh and, for example, open ports. In addition, the package includes network testing utilities such as ping, traceroute, nslookup.

However, many people prefer Fing. The scanner has quite simple and limited functionality, but it is quite enough for the first acquaintance with the network of, say, a cafeteria :). The results display information about available services on remote machines, MAC
addresses and names of hosts connected to the scanned network.

It would seem that everyone has forgotten about Nikto, but why? After all, you can easily install this web vulnerability scanner, written in a script language (namely Perl), via Cydia. This means that you can easily launch it on your jailbroken device from the terminal. Nikto will be happy to provide you with Additional information on the tested web resource. In addition, you can add your own search signatures to its knowledge database with your own hands.
REMOTE CONTROL:

Many network devices (including expensive routers) are managed using the SNMP protocol. This utility allows you to scan subnets for available SNMP services with a previously known community string value (in other words, standard passwords). Note that searching for SNMP services with standard community strings (public/private) in an attempt to gain access to device management is an integral part of any penetration test, along with
identification of the perimeter itself and identification of services.

Two utilities from the same manufacturer are designed to connect to a remote desktop using the RDP and VNC protocols. Similar utilities in App Store There are many, but these are the ones that are especially convenient to use.
PASSWORD RESTORE:
The legendary program that helps millions of hackers around the world “remember” their password has been ported to iOS. Now you can search passwords for services such as HTTP, FTP, Telnet, SSH, SMB, VNC, SMTP, POP3 and many others directly from your iPhone. True, for a more effective attack, it is better to stock up on good brute force dictionaries.
Everyone knows firsthand the vulnerability of using standard passwords. PassMule is a kind of directory that contains all kinds of standard logins and passwords for network devices. They are conveniently organized by vendor name, product, and model, so finding the one you need won't be difficult.
EXPLOITATION OF VULNERABILITIES:
METASPLOIT
www.metasploit.com

It’s hard to imagine a more hacking utility than Metasploit, and that’s what concludes our review today. Metasploit is a package of various tools whose main task is to exploit vulnerabilities in software. Imagine: about 1000 reliable, proven and necessary in Everyday life exploit pentester - right on your smartphone! With the help of such a tool you can really establish yourself in any network. Metasploit not only allows you to exploit flaws in server applications - tools are also available to attack client applications (for example, through the Browser Autopwn module, when a combat payload is inserted into client traffic). Mobile version The toolkit does not exist, but you can install it on an Apple device standard package, using